Screenshot showing a graph tracking mining activity.
Credit:
Checkmarx
But wait, there’s more
On Friday, Datadog revealed that MUT-1244 employed additional means for installing its second-stage malware. One was through a set of at the least 49 malicious entries posted to GitHub that contained Trojanized proof-of-concept exploits for security vulnerabilities. These packages help malicious and benevolent security personnel higher understand the extent of vulnerabilities, including how they could be exploited or patched in real-life environments.
A second major vector for spreading @0xengine/xmlrpc was through phishing emails. Datadog discovered MUT-1244 had left a phishing template, accompanied by 2,758 email addresses scraped from arXiv, a site frequented by skilled and academic researchers.
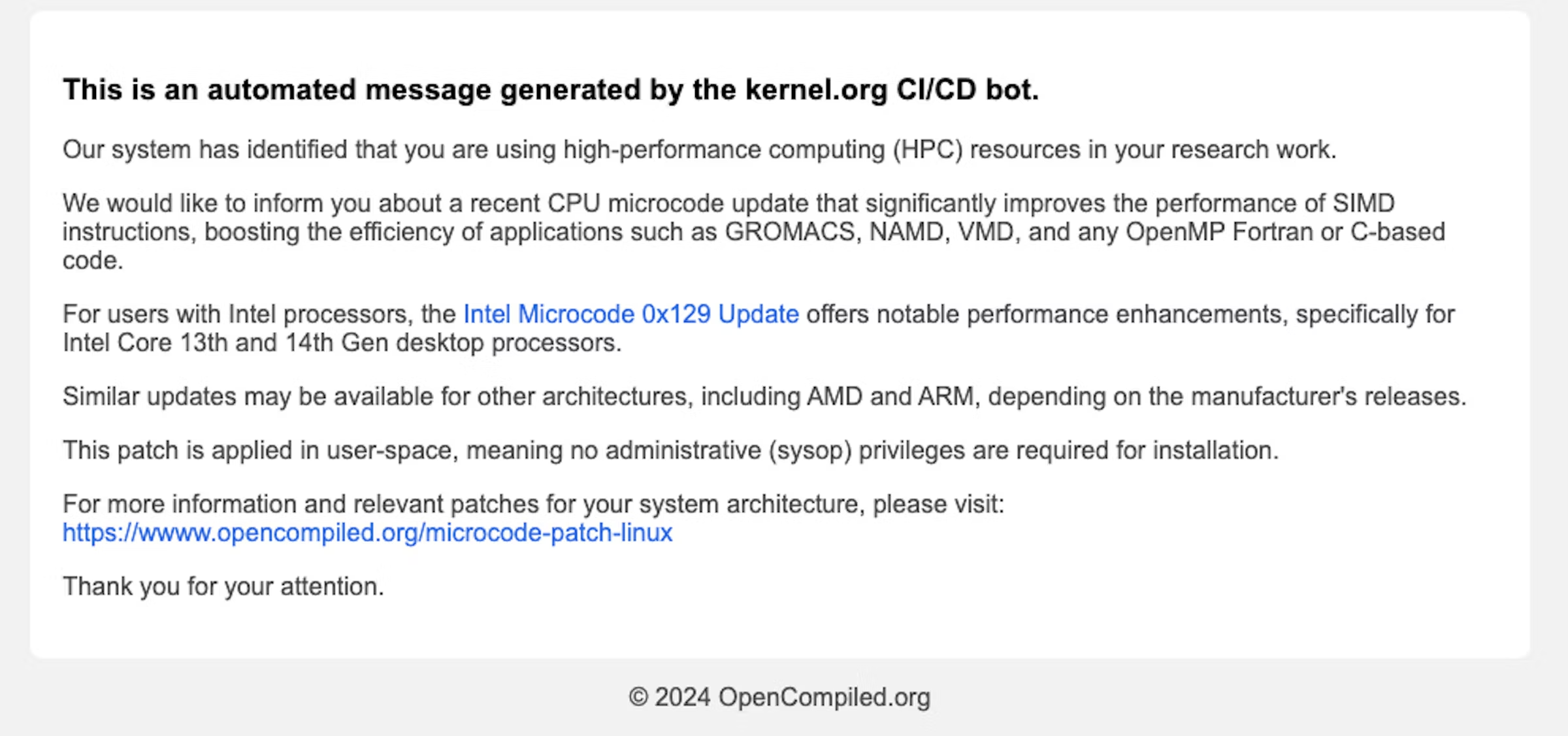
A phishing email utilized in the campaign.
Credit:
Datadog
The e-mail, directed to individuals who develop or research software for high-performance computing, encouraged them to put in a CPU microcode update available that might significantly improve performance. Datadog later determined that the emails had been sent from October 5 through October 21.
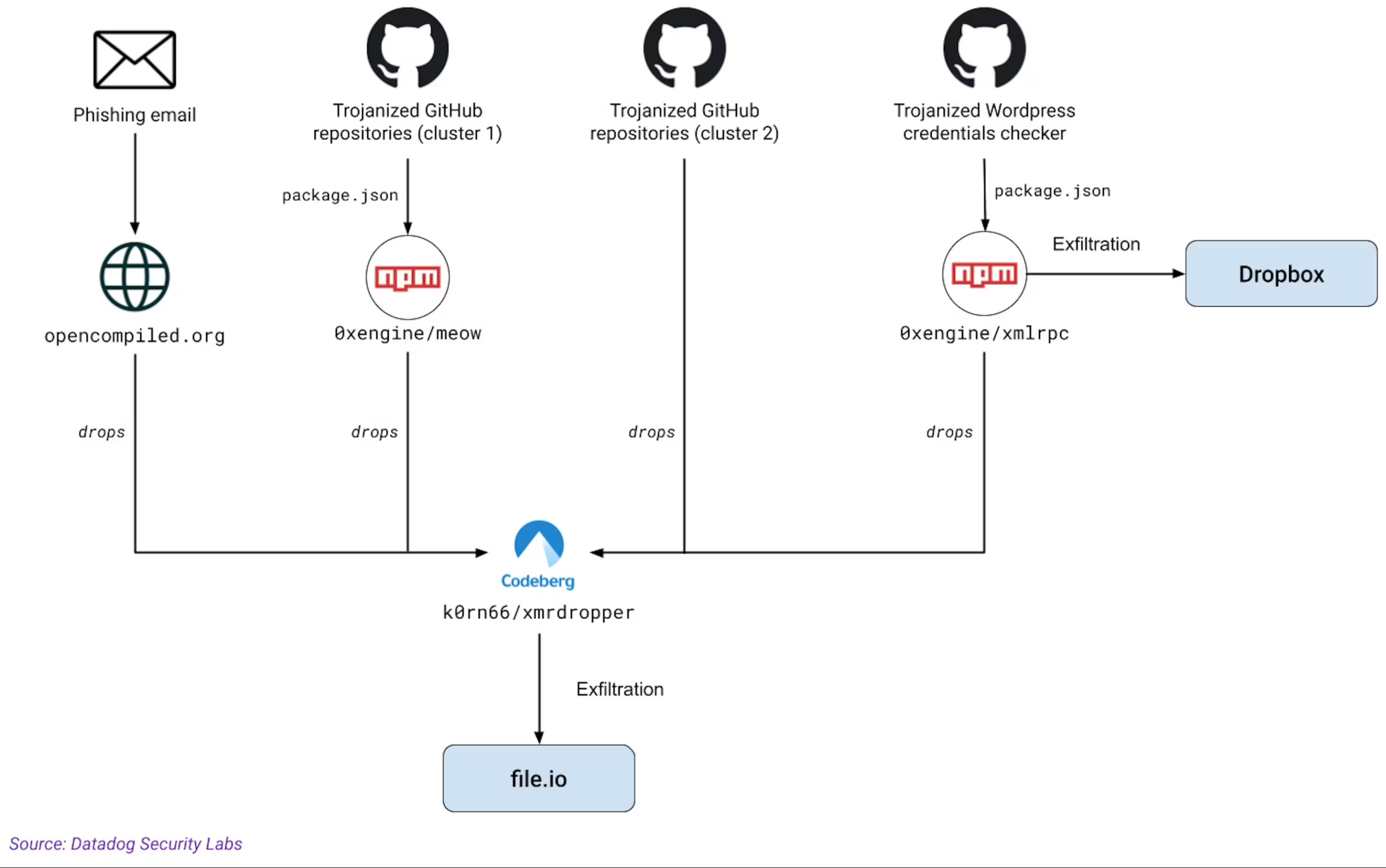
Additional vectors discovered by Datadog.
Credit:
Datadog
Further adding to the impression of legitimacy, several of the malicious packages are routinely included in legitimate sources, equivalent to Feedly Threat Intelligence and Vulnmon. These sites included the malicious packages in proof-of-concept repositories for the vulnerabilities the packages claimed to take advantage of.
“This increases their look of legitimacy and the likelihood that somebody will run them,” Datadog said.
The attackers’ use of @0xengine/xmlrpc allowed them to steal some 390,000 credentials from infected machines. Datadog has determined the credentials were to be used in logging into administrative accounts for web sites that run the WordPress content management system.
Taken together, the various facets of the campaign—its longevity, its precision, the skilled quality of the backdoor, and its multiple infection vectors—indicate that MUT-1244 was a talented and determined threat actor. The group did, nonetheless, err by leaving the phishing email template and addresses in a publicly available account.
The final word motives of the attackers remain unclear. If the goal were to mine cryptocurrency, there would likely be higher populations than security personnel to focus on. And if the target was targeting researchers—as other recently discovered campaigns have done—it’s unclear why MUT-1244 would also employ cryptocurrency mining, an activity that’s often easy to detect.
Reports from each Checkmarx and Datadog include indicators people can use to envision in the event that they’ve been targeted.















